An informative blog about the importance of user’s data privacy

A consistent finding reported in online privacy research is that an overwhelming majority of people are ‘concerned’ about their privacy when they use the Internet. Therefore, it is important to understand the discourse of Internet users’ privacy concerns, and any actions they take to guard against these concerns. A Dynamic Interviewing Programme (DIP) was employed in order to survey users of an instant messaging ICQ (‘I seek you’) client using both closed and open question formats. Analysis of 530 respondents’ data illustrates the importance of establishing users’ privacy concerns and the reasoning behind these concerns. Results indicate that Internet users are concerned about a wider range of privacy issues than surveys have typically covered. The results do not provide final definitions for the areas of online privacy, but provide information that is useful to gain a better understanding of privacy concerns and actions.
BUT HOW DO WE REALLY KNOW THAT WE ARE AT RISK OF HAVING DATA LEAKAGE?
Yup, you read it right. DATA LEAKAGE. We are now living in a 21st generation world and as the world grows, the technology which had sprouted for over a decade is also becoming stronger and stronger also. We couldn’t avoid the fact that most of our leisure time are spent in chatting, surfing the web and playing games. Most likely, some people are addicted in Facebook, Twitter and Instagram. Well, for me, I did noticed that people are more likely to be possessive of themselves. They tend to post pictures wherever they are. Mostly they take pictures during lunch or dinner then upload it to Facebook. But little do you know that you, yourselves are at a potential risk in data leakage? As you post your pictures, it undergoes different process in the technical servers in the web depending on what site are you uploading at. The servers then process your pictures and sends a lot of encrypted data to their main servers. I am not expert of this technicalities but somehow, I could give you advice on how to avoid these serious things together with my teammates.
Although it’s usually used in the context of data breaches in large companies and institutions, data leakage is a big threat for home users as well. It’s not me that’s saying it, but rather industry reports such as the 2015 Global Data Leakage Report.
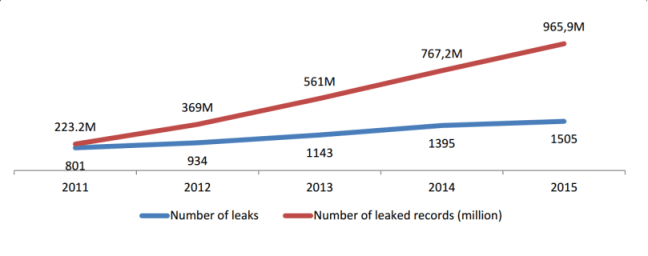
According to Heimdal Securities, there are almost 966 million people which are vulnerable of exposing their data and information to unknown sources or anonymous users swindling out in the web.
In the simplest way, a data leak happens when you lose sensitive information and this loss puts you at risk, whether personally, professionally, emotionally or financially.
Although the term may be used interchangeably with data loss, you should know that data loss sometimes refers more to data that has been destroyed or corrupted. Naturally, the two terms have one thing in common: the fact that the data either ended up in the wrong hands or was irreversibly damaged.
DIFFERENT WAYS A SIMPLE USER COULD BE A POTENTIAL RISK IN THE LOSS OF DATA
1. The browser is where most of the confidential data is extracted from.
The browser is our main gateway to the Internet and it’s probably the most heavily used app on your PC as well. You may not realize that, because it’s part of your daily habit, but cyber criminals know it very well.
So they’ll use your browser’s vulnerabilities to find security holes they can exploit to infect your computer with malware.
Once they’re in, the objective is not just to use the malware to wreak havoc. That’s not a big money-maker (except for ransomware). While one stage of the infection takes control over your system, another phase focuses on extracting as much potentially valuable information as possible.
Mobile devices, removable media (USBs, CDs, external drives, etc.), emails and instant messages are also sources ripe for malicious hacking.
Source: https://infowatch.com/report2015
2. Data leaks are caused intentionally.
While data loss can be accidental (spilling your morning coffee all over your laptop or accidentally deleting a file), data leakage is the consequence of an intended action.
From theft (either digital or physical), to black hat hacking, from sabotage to other malicious acts, someone has to want to steal that information. It can’t just burglarize itself.
3. It is usually caused by malicious outsiders.
According to infowatch.com, Almost 2/3 of the total volume of personal data compromised in 2015 leaked are caused by external attacks. The most notorious incidents of 2015 were associated with illegal actions of hackers, intrusion into companies’ infrastructure, and stealing aggregated data about employees and clients.
4. Downloading and opening attachments from unknown senders.
This is the most prominent reason why most people are vulnerable of data leakage. Opening unwanted documents is not really advisable and is too risky. Unless if you installed some anti-virus softwares into your PC and optimizing, updating and securing your system software.